Author: cslab
-
![[Cloud/Network] GKE’s 34.x Range and EKS’s 100.64.x Range: What Exactly Are They? 🕵️♂️☁️](https://cslab.cloudsecuritylab.co.kr/wp-content/uploads/2025/12/wrimo-image-69452b0c4ee98.png)
[Cloud/Network] GKE’s 34.x Range and EKS’s 100.64.x Range: What Exactly Are They? 🕵️♂️☁️
Hello! Today, we’re going to talk about the “unfamiliar IP ranges” you might encounter at least once when dealing with cloud-native environments. When operating Kubernetes, you might sometimes wonder, “Huh? Our company’s VPC range is 10.0.0.0/16, but why is a 34.x.x.x showing up?” or “Why are AWS EKS pod IPs 100.64.x.x?” These two cases arise…
-
![[Istio] Huh? Where did my istio-proxy go? 🧐 – A Deep Dive into Kubernetes Native Sidecars](https://cslab.cloudsecuritylab.co.kr/wp-content/uploads/2025/12/wrimo-image-69452a9feb800.png)
[Istio] Huh? Where did my istio-proxy go? 🧐 – A Deep Dive into Kubernetes Native Sidecars
Hello! Today, we’re going to dive deep into the “Mystery of the Missing Sidecar Container”, a situation that engineers working with Kubernetes and Istio environments might have encountered at least once. What if you injected Istio, but the proxy container isn’t visible in the YAML file, yet `kubectl` shows it normally? It’s not a bug.…
-
![[Kubernetes] My Pod’s ID Has Changed? A Complete Deep Dive into Service Accounts and Projected Volumes 🆔](https://cslab.cloudsecuritylab.co.kr/wp-content/uploads/2025/12/wrimo-image-69452a75b4356.png)
[Kubernetes] My Pod’s ID Has Changed? A Complete Deep Dive into Service Accounts and Projected Volumes 🆔
Hello everyone! Today, we’re going to dive deep into Service Accounts, the fundamental core of Kubernetes security. If you simply thought, “Isn’t that what’s used to grant permissions to Pods?”, you’ll gain a deeper understanding from today’s post. In particular, the concepts of Projected Volumes and Bound Tokens, which have become the standard in recent…
-

DevOps is Dead? The Emergence of Platform Engineering to Save Developers 💀🛠️
Hello everyone! This is your tech guide, here to sharply dissect the latest trends in the IT industry. 👋 If you’ve been on LinkedIn or read international tech blogs recently, you’ve probably often come across the provocative phrase, “DevOps is Dead.” DevOps, which has been considered the golden rule of the IT industry for over…
-
![[Kubernetes] I launched 3 Pods, so why are they all on one node? (The Scheduler’s Secret) 🧐](https://cslab.cloudsecuritylab.co.kr/wp-content/uploads/2025/12/wrimo-image-694498e7d446d.png)
[Kubernetes] I launched 3 Pods, so why are they all on one node? (The Scheduler’s Secret) 🧐
When operating Kubernetes, there are moments when you think, “Huh? Why is this appearing here?” The most common misconception is the belief that “Pods will be distributed evenly (Round-Robin) across nodes.” Today, through the ‘Pod concentration phenomenon’ I personally experienced, I will delve into the invisible logic of how the Kubernetes scheduler actually scores and…
-
![🏗️ [Kubernetes] Why You Shouldn’t Directly Attach Disks to Pods (The Necessity of PV, PVC, SC)](https://cslab.cloudsecuritylab.co.kr/wp-content/uploads/2025/12/wrimo-image-69422503cf494.png)
🏗️ [Kubernetes] Why You Shouldn’t Directly Attach Disks to Pods (The Necessity of PV, PVC, SC)
Hello everyone! Today, we’re going to dive deep into why PV (PersistentVolume), PVC (PersistentVolumeClaim), and SC (StorageClass), which can be called the “flower” of Kubernetes storage, are absolutely necessary. When you first start learning Kubernetes, you might have this question: > _”Wouldn’t it be easier to just directly write the AWS EBS ID or NFS…
-
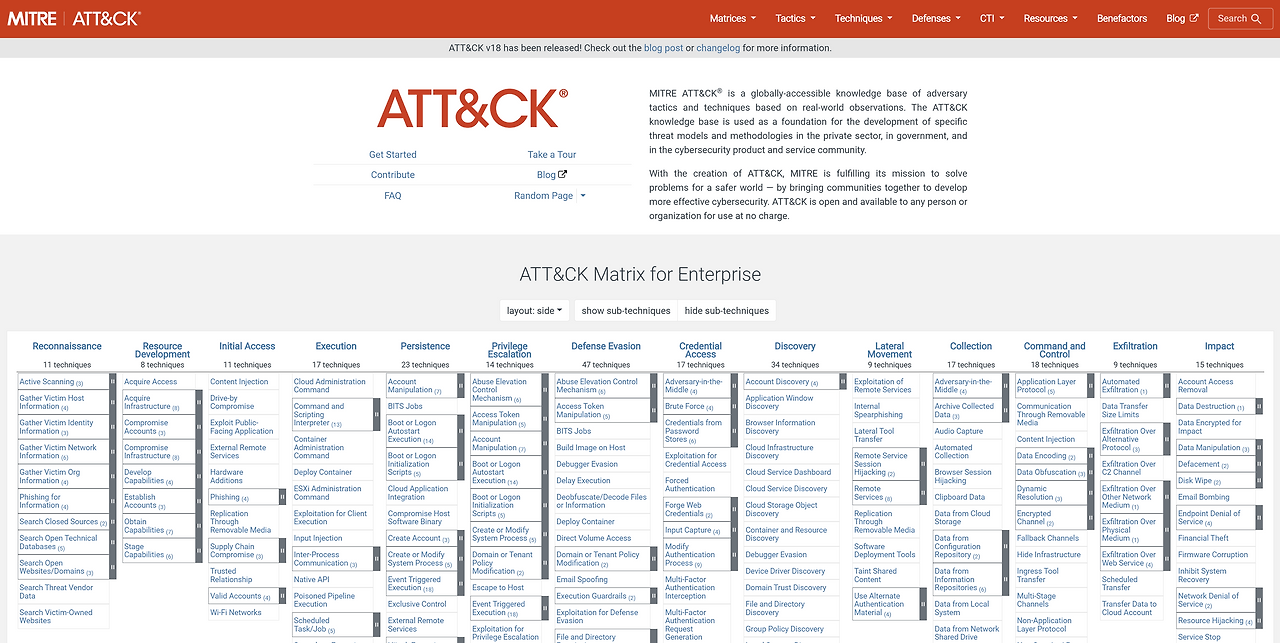
Hackers’ Periodic Table? 🧪 Mastering the MITRE ATT&CK Framework and Mapping Guide
Hello, security researchers who strive for systematic analysis! 🕵️♂️ Until last time, we dissected malware code (static), executed it (dynamic), and visualized logs to uncover every detail of the crime. Now, your notes are probably filled with raw evidence like “wrote a value to the Registry Run key” or “deleted shadow copies with cmd.exe”. But…
-
![🚨 [Breaking News] November 2025, ‘OWASP Top 10 2025’ Finally Revealed – A Complete Analysis!](https://cslab.cloudsecuritylab.co.kr/wp-content/uploads/2025/12/wrimo-image-693febee2843d.png)
🚨 [Breaking News] November 2025, ‘OWASP Top 10 2025’ Finally Revealed – A Complete Analysis!
Hello, security enthusiasts! 👋 After approximately four years since 2021, the OWASP Top 10 2025 (Release Candidate) was officially announced in November. This 2025 version goes beyond simple ranking changes, notably reflecting the recent surge in Supply Chain Attacks and the complexity of Cloud/IaC environments. There are many points to emphasize when teaching Terraform or…
-
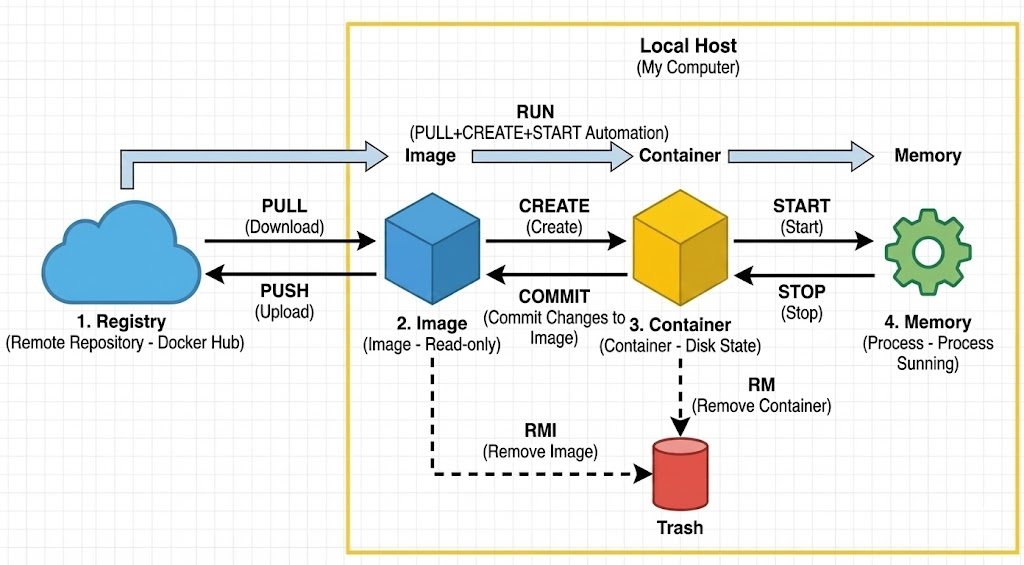
🐳 Docker Life Cycle Complete Guide: From Image to Container Execution and Deletion
Hello everyone! Today, I’d like to provide a very detailed overview of the ‘Docker Life Cycle’, which is fundamental when studying Docker but often confuses many. docker create, docker start, docker run… What exactly is the difference between these seemingly similar commands? 🤔 The answer to this question becomes clear once you understand Docker’s life…
-

🚀 Journey to Golden Kuberstronaut (9/15): CCA Pass, a ‘Close Call’ Victory in Just 6 Working Days! (feat. Unexpected Concepts)
Hello everyone! My steady steps towards becoming a ‘Golden Kuberstronaut’ have finally reached the 9th milestone! After the thrill of passing ICA with a super high score of 98 points, alongside the miracle of my fourth child’s birth, this time I challenged myself with the CILIUM (CCA) certification, which is key to Kubernetes networking. 🥳…