Hello, security enthusiasts! 👋 After approximately four years since 2021, the OWASP Top 10 2025 (Release Candidate) was officially announced in November.
This 2025 version goes beyond simple ranking changes, notably reflecting the recent surge in Supply Chain Attacks and the complexity of Cloud/IaC environments. There are many points to emphasize when teaching Terraform or Kubernetes!
From the newly changed #1 to #10, we’ve extracted and summarized only the key points. 🚀
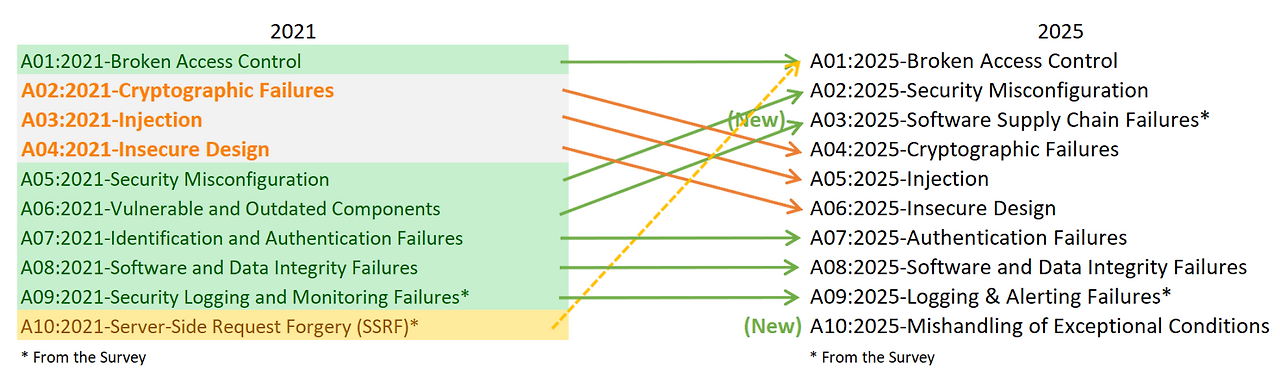
📊 OWASP Top 10 2025: What Has Changed?
The most notable changes are the rise of ‘Supply Chain Security’ and the introduction of a new category, ‘Mishandling of Exceptional Conditions’. SSRF (Server-Side Request Forgery) has been absorbed into other items, and more fundamental software robustness issues have taken its place.
🔥 #1 ~ #3: The Big Three Absolute Threats
🥇 A01:2025 – Broken Access Control
- No Change (Undisputed #1) 👑
- Still the most commonly found and most critical vulnerability.
- This includes cases where IAM permissions are overly broad in cloud environments (Over-privileged), or where vertical/horizontal privilege escalation is not prevented. (Note: SSRF, which was #10 in 2021, has been merged into this item.)
🥈 A02:2025 – Security Misconfiguration
- Rank Soars (5th ➡️ 2nd) 📈
- This is due to the increasing complexity of configuration files (YAML, HCL, etc.) with the spread of cloud-native environments.
- Includes using default accounts, opening unnecessary ports, and public cloud storage configurations. The IaC (Terraform) security that instructors emphasize must shine here!
🥉 A03:2025 – Software Supply Chain Failures
- Major Overhaul (Replaces existing ‘Vulnerable and Outdated Components’) 🔄
- It’s not just about “using old libraries”.
- It has expanded into a much more comprehensive concept, including CI/CD pipeline contamination, malicious packages (Typosquatting), and build tool integrity. Recent incidents like the xz backdoor crisis are major reasons for its rise in rank.
🛡️ #4 ~ #6: Flaws in Design and Implementation
4️⃣ A04:2025 – Cryptographic Failures
- Rank Drop (2nd ➡️ 4th) 📉
- Although the rank has dropped, its importance remains. This includes sensitive data exposure, use of weak cryptographic algorithms, and inadequate certificate management.
5️⃣ A05:2025 – Injection
- Rank Drop (3rd ➡️ 5th) 📉
- Includes SQL Injection, OS Command Injection, etc.
- While its frequency has decreased with the recent use of ORMs and advancements in frameworks, it remains a threat in legacy systems. (LLM Prompt Injection is sometimes treated as a separate category, but broadly speaking, it can be included here.)
6️⃣ A06:2025 – Insecure Design
- Rank Drop (4th ➡️ 6th) 📉
- This is a case where “the design was flawed from the start, not just the coding”.
- Includes lack of Threat Modeling, flaws in business logic, etc.
⚠️ #7 ~ #10: Blind Spots in Authentication and Operations
7️⃣ A07:2025 – Authentication Failures
- The name has been slightly simplified. (Identification omitted)
- All login-related issues, such as weak password policies, lack of MFA implementation, and inadequate session management.
8️⃣ A08:2025 – Software or Data Integrity Failures
- Deals with issues such as fetching code from untrusted sources, failed firmware update verification, and insecure deserialization problems.
- Closely related to A03 (Supply Chain).
9️⃣ A09:2025 – Logging & Alerting Failures
- This is an issue where attacks go unlogged or alarms aren’t triggered, leading to delayed responses.
- An essential item from a Security Operations (SecOps) perspective.
🔟 A10:2025 – Mishandling of Exceptional Conditions
- 🆕 NEW! A completely new category 🌟
- It consolidates previously scattered error handling issues.
- Covers cases where sensitive information like stack traces is exposed in error messages, or where security procedures are bypassed (Fail Open) instead of the system failing safely when an error occurs.
💡 Key Takeaways for Instructors
- Supply Chain Security (A03) is the key keyword: Beyond simply running
npm audit, CI/CD pipeline security and SBOM (Software Bill of Materials) management are now essential. - Elevation of Configuration Errors (A02): When teaching cloud/Kubernetes, emphasize the importance of automation tools (OPA, Kyverno, etc.) to prevent Misconfiguration.
- New Category for Exceptional Conditions (A10): Developers must be educated that “elegant error handling” is as directly linked to security as “feature implementation”.
The OWASP Top 10 2025 reflects modern development trends very well. It would be beneficial to update your curriculum based on these changes! 👍
Leave a Reply