Hello, security researchers who strive for systematic analysis! 🕵️♂️
Until last time, we dissected malware code (static), executed it (dynamic), and visualized logs to uncover every detail of the crime. Now, your notes are probably filled with raw evidence like “wrote a value to the Registry Run key” or “deleted shadow copies with cmd.exe”.
But what if you need to report this information to a security team in the US, or to your company’s executives? If you just say, “Uh… the file wrote and deleted some stuff!”, no one will understand, right? 😅
This is where a ‘standard language’, commonly used by security professionals worldwide, becomes necessary. That is the MITRE ATT&CK framework.
Today, we will delve into what this framework, which organizes hacker attack techniques like an encyclopedia, is, and how we ‘map’ the malicious activities we’ve found to this framework. 🗺️
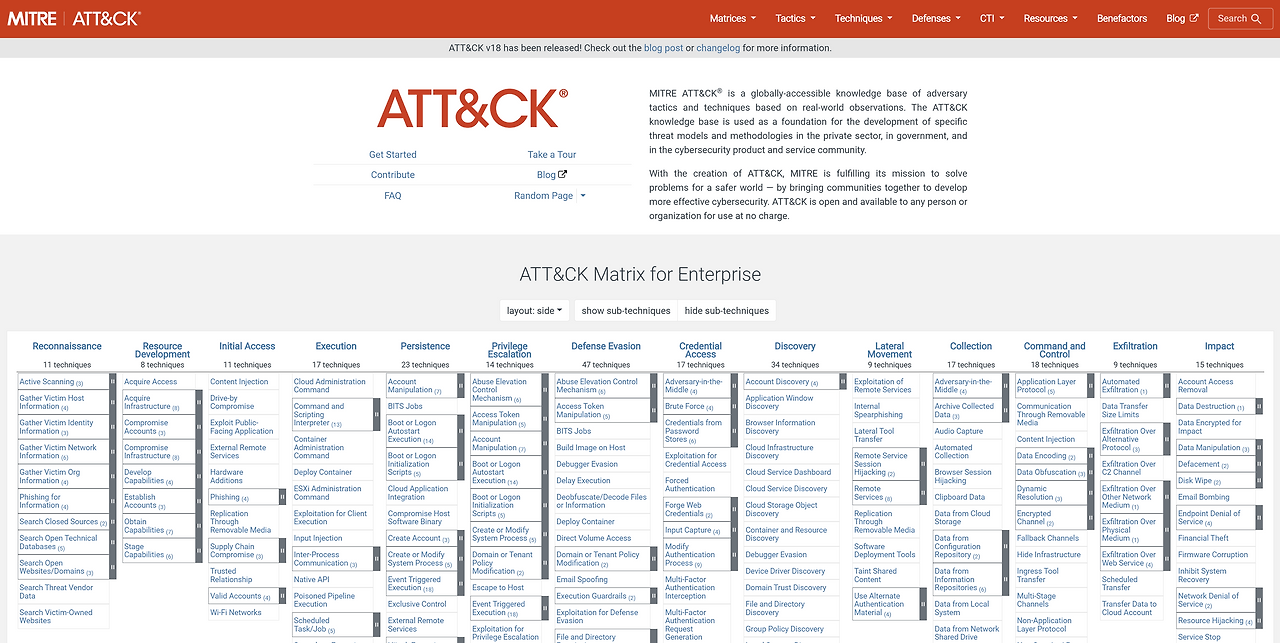
1. What is MITRE ATT&CK? 🌍
MITRE ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. Simply put, it is a “globally accessible knowledge base of adversary tactics and techniques based on real-world observations”.
If chemistry has the ‘Periodic Table of Elements’, cyber security has the ‘ATT&CK Matrix’. It categorizes all stages of a hacker’s process, from initial intrusion to data exfiltration, step by step.
The core structure of this framework consists of three elements called TTPs.
📌 TTPs Structure (Key!)
- Tactic (WHY): What is the attacker’s objective?
- Ex: “I want to stay on this system (Persistence)”, “I want to steal passwords (Credential Access)”
- Technique (HOW): What method was used to achieve that objective?
- Ex: “I’ll hide a file in the startup folder”, “I’ll perform keylogging”
- Procedure (EXACTLY HOW): What is the specific action that implemented the technique?
- Ex: setup.exe entered the path to malware.exe in the registry HKCURun key.
2. Overview of the 14 Main Tactics 🏗️
There are 14 stages according to the attack lifecycle. We must first identify which of these our analyzed activity belongs to.
- Reconnaissance: Information gathering before an attack
- Resource Development: Preparing attack tools (e.g., purchasing servers)
- Initial Access: The stage of first entering a system (e.g., phishing emails)
- Execution: Malicious code execution
- Persistence: Surviving even after rebooting ⭐ (Frequently seen in malware analysis)
- Privilege Escalation: Gaining administrator privileges
- Defense Evasion: Avoiding antivirus or log detection ⭐
- Credential Access: Stealing ID/PW
- Discovery: Understanding internal network structure
- Lateral Movement: Moving to an adjacent PC or server
- Collection: Gathering important data
- Command and Control (C2): Communicating with the hacker’s server and receiving commands ⭐
- Exfiltration: Exfiltrating data outside
- Impact: System destruction (e.g., ransomware encryption)
3. [Practical Theory] Converting My Analysis Results to IDs (Mapping Method) 🔄
Now, let’s simulate the process of converting the logs we found in previous exercises into MITRE ATT&CK IDs. This process is called ‘mapping’.
📝 Case 1: Registry Autostart Registration
- Observed Behavior: malware.exe added a value to the HKCUSoftwareMicrosoftWindowsCurrentVersionRun key.
- Step 1 (Why – Tactic): Why did it do that? ➡️ To execute even after rebooting! ➡️ Persistence (TA0003)
- Step 2 (How – Technique): How did it do that? ➡️ It tampered with a registry run key! ➡️ Boot or Logon Autostart Execution (T1547)
- Step 3 (Detail – Sub-technique): More specifically? ➡️ Registry Run Keys / Startup Folder (T1547.001)
👉 Result: This activity is the T1547.001 technique.
📝 Case 2: Deleting Shadow Copies
- Observed Behavior: Executed command: cmd.exe /c vssadmin.exe Delete Shadows /All /Quiet.
- Step 1 (Why – Tactic): Why did it do that? ➡️ To prevent recovery! (Causing system impact) ➡️ Impact (TA0040)
- Step 2 (How – Technique): How did it do that? ➡️ It crippled system recovery functions! ➡️ Inhibit System Recovery (T1490)
👉 Result: This activity is the T1490 technique.
4. Why is this mapping necessary? 🤷
“Why can’t I just write it out? Why do I need to memorize numbers like T1547?”
- Global Common Language: If an analyst in Korea writes “T1547 found”, a security operator in the US will immediately understand, “Ah, the registry was tampered with.”
- Attribution:
- Malware A: Uses T1059, T1547, T1071
- North Korean hacker group (Lazarus): Frequently uses T1059, T1547, T1071
- Conclusion: We can infer, “This malware is highly likely to be the work of Lazarus!”
- Establishing Defense Strategies: You can formulate specific countermeasures like, “Our company is vulnerable to T1547 (registry) attacks. Let’s create detection rules to block this.”
- MITRE ATT&CK Website: Enter keywords like “Registry”, “PowerShell” into the search bar, and it will find the corresponding technique ID.
- MITRE ATT&CK Navigator: A visualization tool that allows you to color and organize attack techniques like an Excel spreadsheet on the web.
- Utilize AI: This is what we do best, right? Ask AI, “Find the MITRE ATT&CK ID corresponding to this log activity,” and it will find it in a second.
- Before: “Files were created, the registry was tampered with, and it communicated with a strange server.”
- After: “This sample performs Persistence (T1547.001) and establishes a C2 (T1071) channel.”
5. Pro Tip: Don’t Memorize Everything! Use Tools 🛠️
You can’t memorize all 14 tactics and over 600 techniques. (I can’t either! 😵)
🎉 Conclusion: The Final Puzzle Piece for Report Writing 🧩
Today, we learned the theory of converting malicious activities into ‘standardized IDs’.
Now, your analysis notes will change like this:
Doesn’t that sound professional? 😎
All preparations are now complete. Next time, for the grand finale! We’ll see you in the [Practical] “Automatically Generating a Perfect Malware Analysis Report by Integrating All Analysis Information and ATT&CK IDs” episode.
Until the day your analysis becomes a global standard! Fighting! 🛡️✨
Leave a Reply